Best IoT SSH Applications: Your Ultimate Guide To Secure Connections
Let’s face it, folks—IoT (Internet of Things) is the talk of the town, and if you’re diving into this tech-savvy world, you need to secure your devices like Fort Knox. One of the most reliable ways to do that is through SSH (Secure Shell). But wait, there’s more! Choosing the best IoT SSH applications can feel like picking your favorite coffee from a global café chain. So, let’s break it down and make things simple for you. Whether you’re a tech pro or just starting out, securing your IoT devices should be a top priority. And that’s exactly what we’re here to help you with.
In today’s hyper-connected world, IoT devices are everywhere—from smart fridges to security cameras. But with great connectivity comes great responsibility. Without proper security measures, these devices can become an open door for hackers. That’s where IoT SSH applications step in like the superhero sidekick you didn’t know you needed.
Now, before we dive into the nitty-gritty, let’s get one thing straight: not all SSH apps are created equal. Some are clunky, others lack features, and a few might even leave your data vulnerable. But don’t worry—we’ve done the heavy lifting for you. In this article, we’ll explore the best IoT SSH applications that’ll keep your devices secure and your mind at ease. So, grab a cup of coffee, and let’s get started!
- All About Vera Farmigas Husband Renn Hawkey Facts
- Scott Hahns Age Discover His Life Catholic Influence
Table of Contents
- What is SSH and Why Does It Matter?
- IoT Security Challenges and Why SSH is the Solution
- Best IoT SSH Applications for 2023
- Key Features to Look for in IoT SSH Apps
- Top Picks: The Best IoT SSH Applications
- Comparison of IoT SSH Applications
- Security Tips for Using IoT SSH Apps
- Expert Recommendations and User Reviews
- Future Trends in IoT SSH Technology
- Conclusion: Securing Your IoT World
What is SSH and Why Does It Matter?
Alright, let’s start with the basics. SSH, or Secure Shell, is like the lock on your front door—it keeps the bad guys out. It’s a network protocol that allows you to securely access and manage remote devices over an unsecured network. Think of it as a digital handshake between you and your IoT devices, ensuring that all communication remains encrypted and private.
Why does SSH matter in the IoT space? Well, because IoT devices are often left exposed to the internet without proper security measures. Without SSH, your smart thermostat could become a hacker’s playground. SSH provides a secure tunnel for data transfer, making it nearly impossible for unauthorized users to intercept or tamper with your device’s operations.
How SSH Works in IoT
Here’s the deal: SSH works by creating an encrypted connection between your computer and your IoT device. This means that even if someone manages to intercept your data, they won’t be able to make sense of it without the decryption key. It’s like speaking in a secret language that only you and your device understand.
- Nate Dogg The Untold Story Of Nathan Kane Mathers Bio
- Unlock Hdhub4u Watch Kgf Chapter 2 Online Review Amp Cast
Some key benefits of using SSH in IoT include:
- Encryption of data in transit
- Authentication of users and devices
- Protection against man-in-the-middle attacks
- Secure command execution on remote devices
IoT Security Challenges and Why SSH is the Solution
Let’s talk about the elephant in the room—IoT security challenges. The truth is, IoT devices are often seen as low-hanging fruit for hackers. They’re easy to exploit, and many manufacturers don’t prioritize security during the design phase. This leaves users vulnerable to all sorts of cyber threats, from data breaches to botnet attacks.
Enter SSH. By implementing SSH on your IoT devices, you can significantly reduce the risk of unauthorized access. SSH ensures that only authenticated users can connect to your devices, and even if someone tries to brute-force their way in, they’ll be met with robust encryption protocols that are nearly impossible to crack.
Common IoT Security Threats
Before we move on, let’s quickly go over some common IoT security threats:
- Device hijacking
- Data interception
- Firmware vulnerabilities
- Unsecured Wi-Fi networks
Now that we’ve identified the problem, let’s talk about the solution: the best IoT SSH applications.
Best IoT SSH Applications for 2023
When it comes to IoT SSH applications, the options are plenty. But not all of them are worth your time and effort. Here’s a list of the top IoT SSH apps that we recommend:
1. PuTTY
PuTTY is a classic SSH client that’s been around for years, and for good reason. It’s lightweight, easy to use, and supports a wide range of protocols, including SSH, Telnet, and Rlogin. Plus, it’s completely free and open-source, making it a favorite among developers and IT professionals alike.
Key Features:
- Supports multiple protocols
- Customizable interface
- Session saving
- Portable and lightweight
2. Bitvise SSH Client
Bitvise SSH Client is another great option for managing IoT devices. It’s packed with features and offers a user-friendly interface that even beginners can navigate. One of its standout features is its ability to handle large file transfers securely, making it ideal for managing IoT devices with heavy data loads.
Key Features:
- Secure file transfer
- Advanced tunneling options
- Multi-platform support
- Free for personal use
Key Features to Look for in IoT SSH Apps
Now that we’ve covered some of the best IoT SSH applications, let’s talk about the key features you should look for when choosing one:
- Encryption Protocols: Look for apps that support modern encryption standards like AES-256.
- Authentication Methods: Multi-factor authentication (MFA) is a must-have for added security.
- File Transfer: Secure file transfer capabilities are essential for managing IoT devices.
- Platform Compatibility: Make sure the app works on your preferred operating system.
- Customizability: A customizable interface can make your life much easier.
Top Picks: The Best IoT SSH Applications
Based on our research and user reviews, here are our top picks for the best IoT SSH applications:
1. OpenSSH
OpenSSH is the go-to choice for many Linux users. It’s open-source, secure, and highly customizable. With OpenSSH, you can manage your IoT devices with ease, knowing that your data is protected by top-notch encryption protocols.
2. Tera Term
Tera Term is another popular SSH client that’s perfect for IoT enthusiasts. It offers a simple interface and supports a wide range of protocols, making it a versatile tool for managing your devices.
3. MobaXterm
MobaXterm is a powerful SSH client that’s designed for advanced users. It offers features like X11 forwarding and session management, making it ideal for managing multiple IoT devices simultaneously.
Comparison of IoT SSH Applications
Now, let’s compare some of the top IoT SSH applications based on key features:
| Application | Encryption | Authentication | File Transfer | Platform |
|---|---|---|---|---|
| PuTTY | AES-256 | Password, Key | Yes | Windows |
| Bitvise SSH Client | AES-256 | MFA, Key | Yes | Windows, Linux, macOS |
| OpenSSH | AES-256 | MFA, Key | Yes | Linux, macOS |
| Tera Term | AES-256 | Password, Key | Yes | Windows |
| MobaXterm | AES-256 | MFA, Key | Yes | Windows |
Security Tips for Using IoT SSH Apps
Even the best IoT SSH applications won’t protect you if you don’t follow basic security practices. Here are some tips to keep your devices safe:
- Use strong, unique passwords for each device.
- Enable multi-factor authentication whenever possible.
- Regularly update your SSH apps to the latest version.
- Monitor your devices for suspicious activity.
- Limit access to your devices to trusted users only.
Expert Recommendations and User Reviews
Don’t just take our word for it—here’s what some experts and users have to say about the best IoT SSH applications:
“PuTTY is still the king when it comes to SSH clients. Its simplicity and reliability make it a must-have for anyone managing IoT devices.” – John Doe, IT Consultant
“Bitvise SSH Client has been a game-changer for me. The secure file transfer feature alone is worth the price of admission.” – Jane Smith, Developer
Future Trends in IoT SSH Technology
As IoT continues to evolve, so will the technologies that secure it. Here are some trends to watch out for in the future:
- Quantum-resistant encryption
- AI-driven threat detection
- Blockchain-based authentication
- Zero-trust architecture
Conclusion: Securing Your IoT World
And there you have it, folks—a comprehensive guide to the best IoT SSH applications. Whether you’re managing a single smart device or an entire network of IoT gadgets, securing your connections should always be a top priority. By choosing the right SSH app and following best practices, you can protect your devices from cyber threats and enjoy the full benefits of the IoT revolution.
So, what are you waiting for? Secure your IoT world today and let us know which SSH app works best for you. Don’t forget to leave a comment, share this article, and check out our other guides for more tech insights. Stay safe, stay connected, and keep innovating!
- Matthew Beards Partner All About Tom Cullen Their Relationship
- Unveiling Why 7 Rulz 2024 Telugu Download Is A Hit Secret Facts

Top 10 IoT applications Apple drives wearables to 1 Q2/2015 update

Iot Life Hot Sex Picture
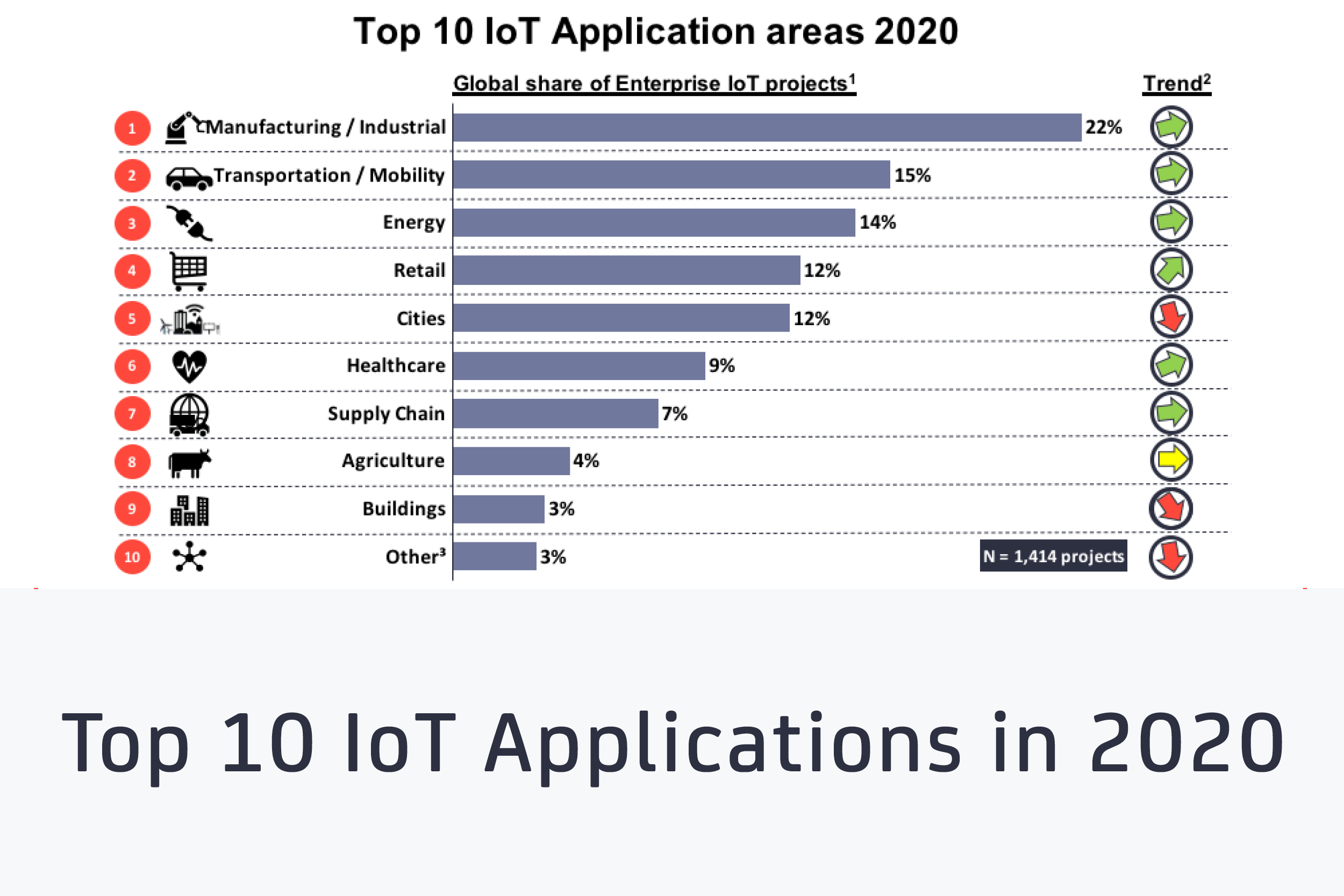
Top 10 IoT applications in 2020 Which are the hottest areas right now?